Question 1
1. Consider the poset ({3,5,9,15,24,45},|).
Which of the following is correct for the given poset?
Answer : (4) There does not exist a greatest element and a least element Which of the following is correct for the given poset?
| Previous | Next |
| UGC NET CS 2019 June - II | UGC NET CS 2019 June - II Question 2 |


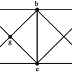


The division symbol ‘|’ is a partial ordering on the set {3,5,9,15,24,45}.
Lets draw Hasse Diagram for the given partially ordered set, or poset.
For given poset, We can not choose greatest element because there are two maximal elements 24 and 45.
Similarly, We can not choose here least element because there are two minimal elements 5 and 3 at same level in Hasse diagram.
So, there is no possibility of greatest and least element.
So, option (4) is correct answer
Reference : Partial Orderings - partially ordered set / poset
Reference : Greatest element of a subset S of a partially ordered set (poset)