Question 1
Which of the learning outcomes are intended in teaching organized at understanding level?
| Previous | Next |
| UGC NET CS December 2019 - Question 1 | UGC NET CS Dec 2019 - Question 2 |
| Previous | Next |
| UGC NET CS December 2019 - Question 1 | UGC NET CS Dec 2019 - Question 2 |
| Previous | Next |
| UGC NET CS December 2019 - Question 144 | UGC NET CS December 2019 - Question 146 |
| Previous | Next |
| UGC NET CS December 2019 - Question 121 | UGC NET CS December 2019 - Question 123 |
| Previous | Next |
| UGC NET CS December 2019 - Question 141 | UGC NET CS December 2019 - Question 143 |
 |
| Add caption |
| Previous | Next |
| UGC NET CS December 2019 - Question 140 | UGC NET CS December 2019 - Question 142 |
| List I | List II |
| a. Functionality | i. Relationship between level of performance and amount of resources |
| b. Reliability | ii. Characteristics related with achievement of purpose |
| c. Efficiency | iii. Effort needed to make for improvement |
| d. Maintainability | iv. Capability of software to maintain |
| Previous | Next |
| UGC NET CS December 2019 - Question 132 | UGC NET CS December 2019 - Question 134 |
| Previous | Next |
| UGC NET CS December 2019 - Question 142 | UGC NET CS December 2019 - Question 144 |
| Previous | Next |
| UGC NET CS December 2019 - Question 122 | UGC NET CS December 2019 - Question 124 |
| Previous | Next |
| UGC NET CS December 2019 - Question 123 | UGC NET CS December 2019 - Question 125 |
| Previous | Next |
| UGC NET CS December 2019 - Question 124 | UGC NET CS December 2019 - Question 126 |
| Previous | Next |
| UGC NET CS December 2019 - Question 125 | UGC NET CS December 2019 - Question 127 |
| Previous | Next |
| UGC NET CS December 2019 - Question 126 | UGC NET CS December 2019 - Question 128 |
| Previous | Next |
| UGC NET CS December 2019 - Question 127 | UGC NET CS December 2019 - Question 129 |
| Previous | Next |
| UGC NET CS December 2019 - Question 128 | UGC NET CS December 2019 - Question 130 |
| Previous | Next |
| UGC NET CS December 2019 - Question 129 | UGC NET CS December 2019 - Question 131 |
| List - I | List - II |
| a. Physical layer | i. Provide token management service |
| b. Transport Layer | ii. Concerned with transmitting raw bits over a communication channel |
| c. Session layer | iii. Concerned with the syntax and semantics of the information transmitted |
| d. Presentation layer | iv. True end-to-end layer from source to destination |
| Previous | Next |
| UGC NET CS December 2019 - Question 131 | UGC NET CS December 2019 - Question 133 |
| List I | List II |
| a. Scrum | i. CRC cards |
| b. Adaptive software development | ii. Sprint backlog |
| c. Extreme programming | iii. <action> the <result> <by/for/of/to> a(n) <object> |
| d. Feature-driven development | iv. Time box release plan |
| Previous | Next |
| UGC NET CS December 2019 - Question 133 | UGC NET CS December 2019 - Question 135 |
| List I | List II |
| a. Frame attribute | i. to create ink in HTML |
| b. <tr> tag | ii. for vertical alignment of content in cell |
| c. Valign attribute | iii. to enclose each row in table |
| d. <a> tag | iv. to specify the side of the table frame that display border |
| Previous | Next |
| UGC NET CS December 2019 - Question 134 | UGC NET CS December 2019 - Question 136 |
| List I | List II |
| a. Direct | i. 200 |
| b. Register indirect | ii. 902 |
| c. Index with R1 as the index register | iii. 400 |
| d. Relative | iv. 600 |
| Main Memory | |||||
| Instruction | 500 | Opcode | Mode | ||
| Opcode | 500 | → | 501 | ||
| 502 | Next Instruction | ||||
| ⋮ | |||||
| R1 | 200 | ⋮ | |||
| ⋮ ⋮ | |||||
| Previous | Next |
| UGC NET CS December 2019 - Question 135 | UGC NET CS December 2019 - Question 137 |
| List I | List II |
| a. Isolated I/O | i. same set of control signal for I/O and memory communication |
| b. Memory mapped I/O | ii. separate instructions for I/O and memory communication |
| c. I/O interface | iii. requires control signals to be transmitted between the communicating units |
| d. Asynchronous data transfer | iv. resolve the differences in central computer and peripherals |
| Previous | Next |
| UGC NET CS December 2019 - Question 136 | UGC NET CS December 2019 - Question 138 |
| List I | List II |
| (a) Micro operation | (i) Specify micro operations |
| (b) Micro programmed control unit | (ii) Improve CPU utilization |
| (c) Interrupts | (iii) Control Memory |
| (d) Micro instruction | (iv) Elementary operation performed on data stored in registers |
| Previous | Next |
| UGC NET CS December 2019 - Question 137 | UGC NET CS December 2019 - Question 139 |
| Previous | Next |
| UGC NET CS December 2019 - Question 138 | UGC NET CS December 2019 - Question 140 |
| Previous | Next |
| UGC NET CS December 2019 - Question 139 | UGC NET CS December 2019 - Question 141 |
| Previous | Next |
| UGC NET CS December 2019 - Question 143 | UGC NET CS December 2019 - Question 145 |
| Previous | Next |
| UGC NET CS December 2019 - Question 145 | UGC NET CS December 2019 - Question 147 |
| Previous | Next |
| UGC NET CS December 2019 - Question 146 | UGC NET CS December 2019 - Question 148 |
| Previous | Next |
| UGC NET CS December 2019 - Question 147 | UGC NET CS December 2019 - Question 149 |
| Previous | Next |
| UGC NET CS December 2019 - Question 148 | UGC NET CS December 2019 - Question 150 |
| Previous | |
| UGC NET CS December 2019 - Question 149 |
| Previous | Next |
| UGC NET CS December 2019 - Question 130 | UGC NET CS December 2019 - Question 132 |
| Previous | Next |
| UGC NET CS December 2019 - Question 112 | UGC NET CS December 2019 - Question 114 |
| Previous | Next |
| UGC NET CS December 2019 - Question 64 | UGC NET CS December 2019 - Question 66 |
<!DOCTYPE html>
<html>
<head>
<script>
function myFunction() {
document.getElementById("demo").innerHTML = "Hello World!";
document.getElementById("demo").style.color = "blue";
document.getElementById("demo").style.fontSize = "35px";
}
</script>
</head>
<body>
<p>When you click "Try it", a function will be called.</p>
<p>The function will display a message.</p>
<button onclick="myFunction()">Try it</button>
<p id="demo"></p>
</body>
</html>
| Previous | Next |
| UGC NET CS December 2019 - Question 65 | UGC NET CS December 2019 - Question 67 |
| Previous | Next |
| UGC NET CS December 2019 - Question 66 | UGC NET CS December 2019 - Question 68 |
EMPLOYEE (EID, ENAME, DEPTNO)
DEPARTMENT (DEPTNO, DEPTNAME)Select count (*) 'total' from EMPLOYEE
where DEPTNO IN (D1, D2)
group by DEPTNO having count (*) > 5| Previous | Next |
| UGC NET CS December 2019 - Question 71 | UGC NET CS December 2019 - Question 73 |
| Previous | Next |
| UGC NET CS December 2019 - Question 73 | UGC NET CS December 2019 - Question 75 |
| Process | Maximum Needs | Current Needs |
| P0 | 10 | 5 |
| P1 | 4 | 2 |
| P2 | 9 | 2 |
| Process | Maximum Needs | Allocated resources | Remaining Needs |
| P0 | 10 | 5 | 5 |
| P1 | 4 | 2 | 2 |
| P2 | 9 | 2 | 7 |
| Previous | Next |
| UGC NET CS December 2019 - Question 77 | UGC NET CS December 2019 - Question 79 |
Question 16 In a certain coding language. 'AEIOU' is written as 'TNHDZ'. Using the same coding language. 'BFJPV' wil...
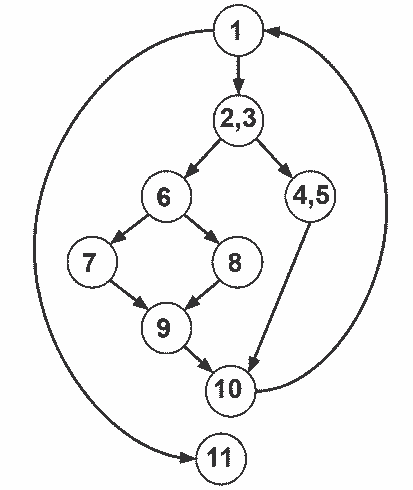
Predicate is a node that contains condition. It means at least 2 outgoing edges required to qualify as a predicate.
Total number of predicates are THREE.
-
The vertex 1 is contains 2 outgoing edges are (2,3) and 11
-
The vertex (2,3) contains 2 outgoing edges are 6 and (4,5)
-
The vertex 6 contains 2 outgoing edges are 7 and 8.
So, option 1 is correct answer